Technology Explanation
ABreach and Attack Simulation Tool
is a security testing software that enables simulating realistic attacks with an automation-oriented approach. The simulation must be standardized, reproducible and allow for continuous testing. The tool aims to examine the system's security and produce results accordingly, outlining vulnerabilities and suggesting mitigations.General Interaction
BAS Tools have different ways to interact with the system, the majority of them adopt an agent-based approach which leverages the structure represented in the image below.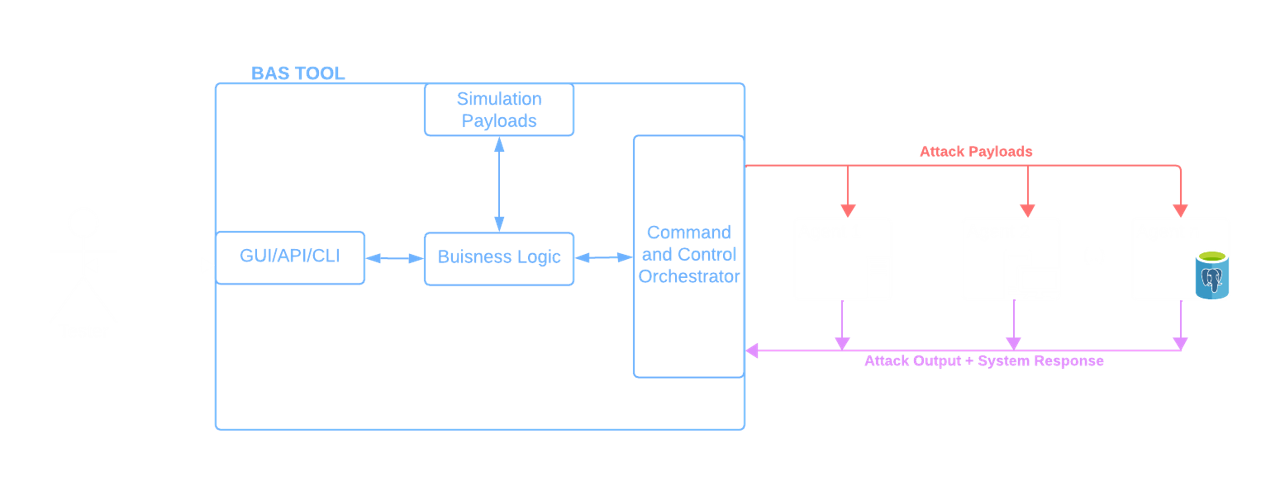
-
Testers
: personnel involved in the simulation interacting with the BAS Tool. The interaction between the tester and the tool depends on the specific functionalities of the tool, which usually offers a graphical user interface. -
BAS Tools
: is the centre of command of all the operations, typically installed directly on devices accessible to testers. The software can communicate with agents and vice-versa by leveraging a command and control channel. There are several ways in which this connection is established, for example, Caldera [16] requires running a payload on the agent system while other solutions require installing a software on the targets. -
Agents
the various elements of the testers' infrastructure that will be the target of the simulation. The type of agents supported depends on the specific solution, and they can be endpoints, personal devices, servers, databases and many more.
Advantages of BAS Tools
It is objective that the amount, complexity and economic damage of cyberattacks is increasing. Therefore, it is essential to shift the paradigm from "avoiding a breach" to "analyzing possible breaches" and testing what attackers can do against our defenses. This shift necessitates the inclusion of both blue teams and red teams in our security strategy. However, traditional red teaming engagements are often slow, difficult to replicate or automate, and consequently very costly. Breach and Attack Simulation (BAS) Tools address these challenges effectively. To summarize, the key benefits of BAS Tools are:- Change security approach to adapt to new threats,
- Improve red teams' efficency, cost, performance,
- Generate objective results about your system's security
- Test performance of acquired security solutions,
- High ROI
Limitations of BAS Tools
The technology is relatively new and faces challenges both due to its novelty and inherent limitations. The principal limitations of the currently available Breach and Attack Simulation Tools are:- Scarce accessibility,
- Improvable automation capabilities,
- Partial effectivness of simulations,
- Leverage of pre-existing exploits to discover vulnerabilities,